Sign Up for the Newsletter
The most up-to-date news and insights into the latest emerging technologies ... delivered right to your inbox!
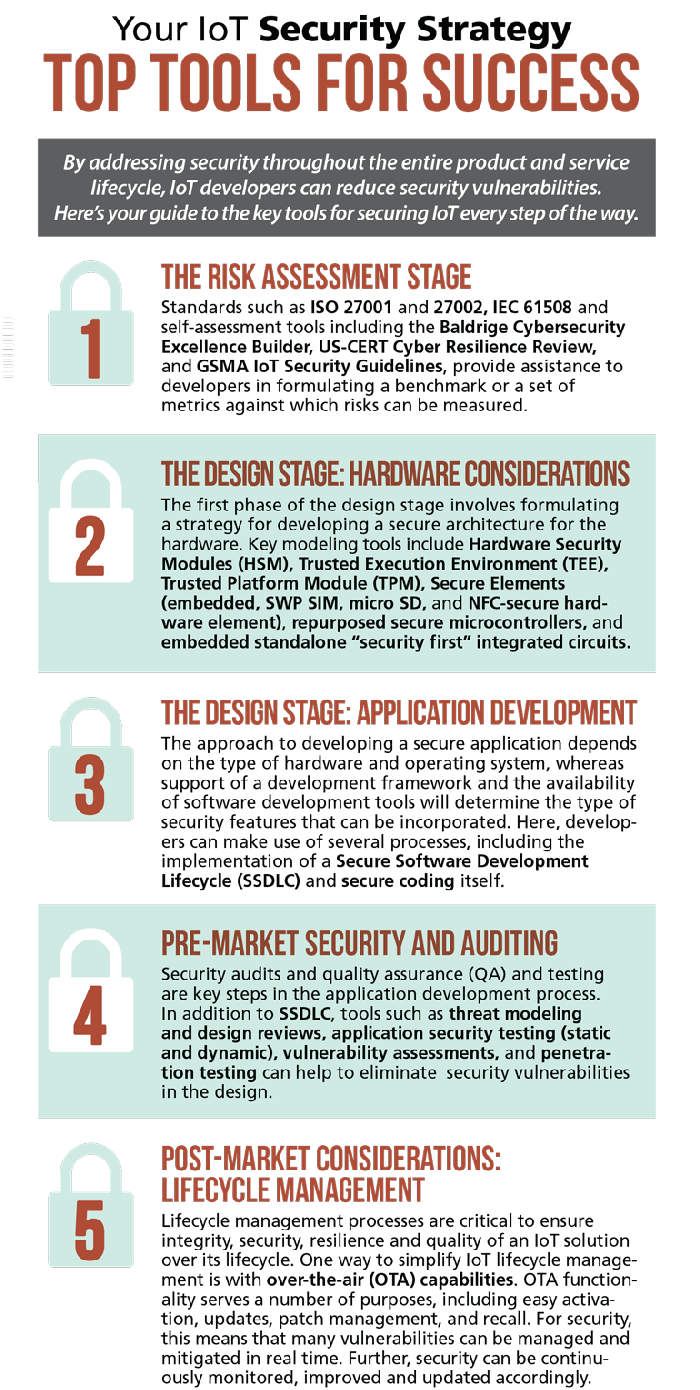
Security isn't something you can accomplish after the fact. Here are five tools you can use to build security into your Internet of Things products.
March 16, 2017

By IOT Content Manager
Much of what is written about IoT security is more hyperbolic than it is helpful. But the fact is there are proven steps you can take to vastly limit security vulnerabilities when developing connected products. Here are five key strategies you can use to do just that, which span from the risk-assessment stage to lifecycle management.
You May Also Like