The nonprofit organization has developed a multifaceted IoT security platform that draws support from academia and Attivo Networks.
August 15, 2019

The adage about an ounce of prevention being worth a pound of cure should apply to IoT security as much as anything else. But often, connected devices ranging from industrial control systems to security cameras to smart door locks offer little in the way of cybersecurity features. Complicating matters further is the fact many organizations and individuals who have deployed IoT devices often have limited awareness of the cyber-risks they pose.
The nonprofit Global Cyber Alliance aims to help change that equation with a new development platform for IoT devices. Founded in 2015 by the Manhattan District Attorney’s Office, the City of London Police and the Center for Internet Security, GCA has introduced on August 15 an Automated IoT Defence Ecosystem. AIDE is designed to help small businesses, manufacturers, service providers and the public spot vulnerabilities and shore up the weak defenses of many IoT defenses.
About two years ago, the organization released a free global DNS infrastructure for protecting the public known as Quad9. “It respects people’s privacy and is currently protecting about 15 million endpoints,” said Adnan Baykal, the global technical advisor at GCA. After the organization released that product, it sought to identify the next area of focus related to global systemic. “And we decided that we were going to do something in IoT,” Baykal said.
For its IoT-focused AIDE initiative, GCA has launched multiple individual efforts designed to feed into each other.
First, it has launched so-called honey farms, groups of honeypots, across the world. In all, the honey farms generate intelligence from more than 1,200 devices.
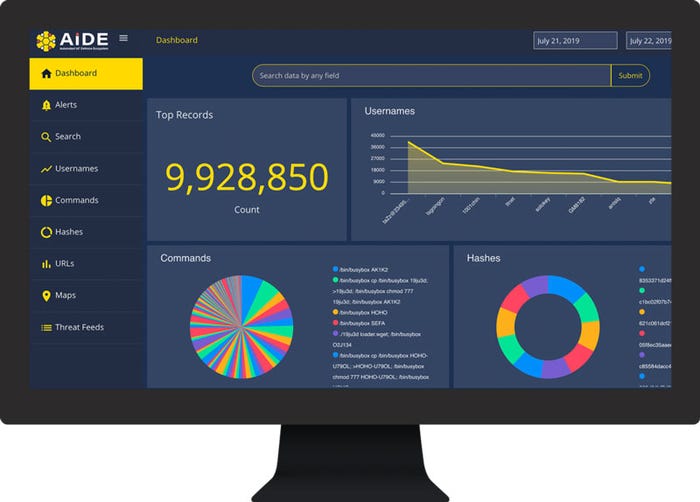
A representation of the type of data the AIDE platform gathers.
Next, GCA is using virtual IoT devices on simulated networks designed to attract attackers. “Our technology enables you to use real IoT devices, and replicate them virtually around the globe,” Baykal said. “You can stand up a DVR camera in the lab, and then replicate that camera virtually in a thousand places around the world.” From an attacker’s perspective, the emulated camera looks like the real deal. “We even put pictures of jewelry, for instance, in front of the camera,” Baykal said. This initiative involves the deployment of what GCA calls ProxyPots, custom IoT honeypot technology.
GCA also integrates data from other IoT honeyfarm in a central location “so everyone using the platform can have a better and bigger view, can analyze the data, and work towards mitigating identified attacks,” Baykal said.
In addition, GCA is opening its platform to vetted academic communities to enable researchers to identify characteristics of attacks that can help shape policies and develop mitigation strategies. “Threat intelligence and insights developed from these partnerships and research is made available to the security communities at large,” Baykal explained.
GCA has also partnered with Attivo Networks, which has granted the organization access to its deception technology. “We are building a honey farm using their SCADA systems,” Baykal said. “So we are doing IIoT with Attivo. We are doing IoT and consumer stuff using ProxyPots.
In addition, GCA is also partnering with other organizations like British Telecom that run IoT honey farms to feed more data into the GCA platform. “We are talking to other organizations who are doing something similar, and convincing them to donate data to this platform,” Baykal said. “The whole idea is: If British Telecom gives us their data, they get access to everything else we have.”
The data collection efforts will provide GCA with a unique perspective on IoT attacks and the ability to publish threat feeds with information relevant to current attacks. Examples of the latter include malware hashes, malicious images and URLs used in attacks. “People can download these data feeds and implement blocks in their IoT and edge devices,” Baykal said.
GCA also wants to partner with academia, giving professors doing data science applied to cybersecurity research fodder for research. “They are eager to get their hands on real attack data to build models,” Baykal explained. To date, the organization has partnered with researchers from Texas A&M and the University College of London. “Academia can get data for their publications, which is what we want. We want to get access to their algorithms so that we can implement those into the platform. We are not selling anything. We just want nonexclusive rights to algorithms so we can further protect networks,” Baykal added. “It’s a win-win.”
About the Author(s)
You May Also Like



.png?width=300&auto=webp&quality=80&disable=upscale)


.png?width=300&auto=webp&quality=80&disable=upscale)