What actions should enterprises take following the Internet outage caused by the huge DDoS attack by the Mirai botnet a few weeks ago?
June 8, 2017

By Steve Bell
Having attended the IoT Security Summit 2016 in Boston last week, it seemed ironic to hear the news on my return about the huge Internet outage caused by the global domain name server (DNS) infrastructure being taken down as a result of a huge DDoS attack by the Mirai botnet.
This botnet compromised IoT devices to launch attacks on targeted web properties. According to Arbor Networks, the security division of NetScout Systems Inc. (Nasdaq: NTCT), this isn't the first time that the Mirai botnet has been used; it was put to work in a sustained and sophisticated large-scale 540Gbit/s attack on Olympic websites during the 2016 Rio Olympic Games. The botnet exploits one of the lesser known IP protocols, Generic Routing Encapsulation (GRE), used for unencrypted ad-hoc VPN-type tunnels. It is protocol number 47 of the 256 Internet protocols. According to an Arbor Networks blog, use of these lesser-known protocols has been slowly increasing since the year 2000, and, more recently, these techniques have been rediscovered and weaponized, and included in botnets for hire.
Given the sophistication and scale of these attacks, and the fact that they are being offered as a service, it means that connected enterprises have to take a holistic view of security as they incorporate enterprise IoT and industrial IoT into their business operations and IT infrastructures. One of the aspects that has to be recognized is the reality that the potential threat surfaces increase significantly because of the dimensions of “things” that are being connected, and because of the diverse types of devices, platforms and players that are being included.
As shown in the table below, enterprise IoT can relate to a significant number of operations associated with buildings and campuses, while industrial IoT can relate to production processes. Additionally, IoT initiatives potentially have to address connected and autonomous vehicles (for instance in warehouses or mining operations), as well as the health and safety aspects of people where connected wearables are intrinsic parts of production or service capabilities.
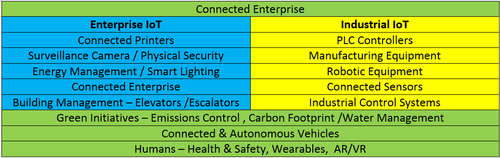
Since it's important that security doesn't impede business, it's becoming increasingly vital that security is built into products and processes by design. This requires an analysis of assets, and an understanding of potential threat models to help determine the security lifecycle of products and their associated business models. Adopting proven frameworks, such as NIST or ISO27001/2, and holding ecosystem partners to the same standards is a security fundamental. Suppliers of equipment must ensure that they incorporate hardware-based security, including chipsets that protect the relevant identifiers, and that meet secure boot requirements for authentication and validation. Additionally, secure storage and secure communications, both within and from the device, have to be assured across the network to the cloud.
The device and network architectures need to take account of the drivers for these two types of operation, which will often differ in terms of response times, need for continuous operation, the lifespan of the assets and whether or not they are operating in a harsh environment. As a result, the traditional homogeneous infrastructure, that enterprises have been familiar with, will fragment into a variety of unique devices, often with specific-purpose hardware, and this can result in the possibility of unique malware and cyber attacks. The traditional approach of being reactive — detecting and blocking these attacks — has to transition to a more intelligent and proactive approach. This uses the context of the IoT solution, combined with machine learning and behavioral analysis, to develop automated mechanisms for discovery and real-time monitoring.
Given the requirement for such sophisticated security capability, it has to be recognized that partnering with network and cloud providers to provide layers of defense should be an intrinsic part of an enterprise IoT security strategy. This is the essence of AT&T Inc. (NYSE: T)'s enterprise security strategy and NetBond, its dynamic secure virtual private networking offering. It articulates a security framework comprising four layers: an endpoint solution, connectivity — which is the VPN Netbond, the data application layer and threat management to detect breaches.
The security offering is an integrated network-based solution, with machine learning built into the network that provides threat intelligence and security data analytics. AT&T has sold this solution to 450 global customers, and has partnered with 16 cloud providers, including the number one cloud provider, AWS, to offer it as a bundled service. Enterprise customers are realizing that, in a digitized world where every physical IoT component has a corresponding cloud component, they need end-to-end guaranteed security and analytics.
You May Also Like


.png?width=700&auto=webp&quality=80&disable=upscale)
.png?width=300&auto=webp&quality=80&disable=upscale)


.png?width=300&auto=webp&quality=80&disable=upscale)