Bridging the chasm between IT and industrial operations’ security paradigms.
June 7, 2017
By Eric Winsborrow
The ability to access a wide variety of industrial data anywhere, widely known as industrial IoT or IIoT, enables companies to improve processes with direct insights and data, decrease service costs through remote access, and increase efficiency and uptime with rule based machine-to-machine communication.
Despite the tremendous opportunities to profit from IIoT, providing access to industrial systems that have traditionally been isolated from the internet obviously introduces numerous risks that must be managed effectively. What may not be as obvious is that the biggest challenges to securing industrial systems from the internet may be the cultural chasm that exists between industrial operations and traditional IT security approaches.
At the Internet of Things World Europe conference in Dublin, Ireland in November 2016, I was one of the “IoT Security Challenges” panelists. It was a very lively discussion with the audience on the significance of IoT cyberattacks. As one would expect, there was no shortage of material with numerous industrial IoT attacks including in which industrial systems were breached with varying levels of exposure. The clear conclusion was that the biggest issues customers face in creating security isn’t necessarily technical, but cultural.
Many executives don�’t realize that there are two technology organizations in their companies. The first technology organization is the one we all think of, information technology (IT). The other is operations technology (OT) referring broadly well beyond manufacturing – utilities, wind and monitoring, switching, pumps and other capital equipment; anything with a sensor, control system industrial network.
To make matters more difficult, neither organization tends to understand, or like, the other organization. Many IT staff are persona non-grata on many operations floors, because of the deep cultural divide. It’s like if a civilian walked into a crime scene and asked a detective “how can I help you?” The answer would be “by getting the heck out of here immediately” (and probably not that polite).
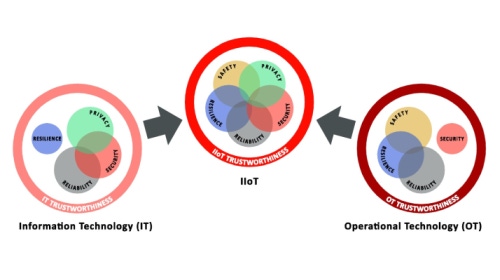
The IT/OT cultural differences might be best explained in this diagram from the Security Working Group of the Industrial Internet Consortium, a global organization founded by companies including Bosch, GE, IBM and Intel to develop a common security framework and methodology to assess security and build a safe, reliable, and secure industrial internet.
The diagram at the top of the page describes the priorities of operational technology being factors like resilience, reliability and physical safety.
Resilience is a level above reliability – it’s the ability to keep running even if certain things “hit the fan”, by wearing out, breaking, or malicious attack. If you are running a factory floor, supplying electric power to a region, or operating the airport baggage system, everything must keep running. If something breaks operations needs to get it working, with duct tape and chewing gum if they must.
For IT, reliability may be important, but complete resilience to outages isn’t the top priority. If network connections are lost or email is down, that’s terrible, but unfortunately, not uncommon, and someone may lose their job but not their life.
For operations, it’s physical – safety outranks security, and to OT security means cameras and actual keys (not encryption keys). Keeping industrial systems safe from outside attack is accomplished by physical security approaches, in other words isolating systems from the outside world. For IT, security is very much aligned with privacy, securing from loss of data, revenues and brand image impacted by a customer data breach. OT doesn’t care about image, they grease wheels literally, turn bolts faster and better, and hit production targets… or not.
Culturally speaking, operations staff do not resonate with the term IoT or understand the game-changing promise that has created such a buzz in Silicon Valley and the IT industry. They’ve heard about IoT, and know it’s a Board initiative, but have no idea how to implement “IoT”. Operations staff, however, do understand the value of connecting outside operations and third party solutions providers to traditionally isolated remote industrial systems to save costs and improve uptime, but need to do this as simply, securely and resiliently as possible.
Industrial operations are all about saving costs
Big data opportunities and other complex buzzwords brought fourth by the IT side of IIoT have yet to gain traction broadly for operations.
The most prominent and immediate opportunity today for operations staff is improving efficiency with simple remote connectivity. At Distrix, we have customers that want to remotely manage industrial robots because they don't want to have the cost of driving or even flying to every customer’s factory floor to analyze performance data and perform preventative maintenance.
It's too costly for them, and the customer wants a faster response. We have customers with oil platforms in the Gulf that are rather difficult to drive to that need monitoring, and natural gas pipelines to manage flow rates. Allowing secure, remote connectivity reduces costs and improves performance of those facilities.
While the IT industry is making noise about the next big IoT thing and analyzing terabytes of big data, operations just wants simple, secure remote connectivity to save costs and improve performance. The problem is that the traditional approach to IT security is a giant pain in their wallets (and where they put their wallets).
Providers in the IoT security space must improve their value to the Industrial operations buyer:
1. Reduce the cost and complexity of simply connecting outside networks
It takes hours (sometimes weeks or months at scale) to create the basic secure connections customers need. Traditional VPNs need to create complex tunnels inside other tunnels just to get access to traditionally isolated industrial networks, and requires the most expensive certified security professionals to perform the task.
If industrial customers are all about saving costs for their operations, it is important that providing secure remote access does not create a cost burden for them to do the work themselves or to pay someone else to do it. This should be minutes, not hours or longer to set up.
2. Reduce the potential points of intrusion – but make it simple
Opening-up industrial systems means exposing them from whatever threat is coming in from the outside. If we allow outside access, we have to reduce the points of intrusion to minimize any risk of impacting the entire customer network. If a robot manufacturer wants remote access to a robot on a factory floor, just give them access to their robot.
Unfortunately, traditional VPN tunnels provide wide-open access to entire networks. VPN stands for “Virtual Private Network”, meaning they were designed to create full access from one network to another and just protect the parts in between, under the assumption that the internet was dangerous, but not the two networks connecting themselves – we know better these days.
Neither network can be sure if some system on the other side is already compromised. Today’s best security posture is to assume that the attackers are already inside.
As it turns out, the OT decision makers’ paranoia is well founded and they don’t want to be anywhere near IT networks. IT networks are flooded with hacks and exploits that make the news every day. So why would OT want to expose themselves?
If OT does solicit support from IT to create the right security environment, the status quo is to use highly trained and expensive network security professionals to create complex “Access Control Lists” (ACLs) to restrict network access down to the originally intended level for the user (e.g. just a device or the data they create). In addition to the combined time and expense in fulfilling a request, the lag in response time can further hinder operations and ultimately return on investment of IIoT initiatives.
In 2017, one would think a simple interface would allow an operations staff member with appropriate clearance to simply log into an interface to select the level of access they want to allow an employee or third party to have, in the protocol they want (like Modbus, which is not IP) and create a secure tunnel in minutes. Common sense is not common practice; there is a surprising lag in simple, user-friendly Industrial IoT tunneling technology.
3. Make it easy for basic Help Desk staff to grant third-party remote access
Ready for a fun security fact? Creating traditional VPN tunnels in order to allow even temporary third-party access often results in remote access to a critical operations network that is never closed!
It’s like drilling the big “Chunnel” between England and France. It’s always wide open, takes a lot of money to create, you can’t turn it off or on. What’s worse, it’s not France on the other side – it’s the entire internet. Of course, if your organization is quite security conscious, each train car that passes through the Chunnel is given permission with the security keys (the RSA token you use with your password when creating your own remote connection). If you don’t use it, the access is still there, and if a bad person has taken over your computer or someone else’s, it’s free and secure passage through the tunnel any time they want.
Wouldn’t it be better to be able to turn the tunnel on and off with a click of a button, and not by some highly paid security programmer, but a help desk person?
That way allowing third party remote access to industrial systems could be less costly to enable, and only be done when the operations customer wanted the access to happen, and for only how long – just a few minutes to collect sensor data or half an hour for preventative maintenance, etc.
Today, however, that tunnel into the network is always open. The operations customer that knows that doesn’t want VPN tunnels into their network – and I’m sure I just scared many others who had no idea that was the case.
4. Passing the burden on to third party cloud and security providers may not help with increased security or cost savings.
Sometimes to make the complexity of all the above issues “go away”, industrial customers turn to third party VPN providers and cloud access companies, but in doing that they aren’t solving the problem, just passing it along onto others for convenience.
Now these tunnels are permanently open and sitting in someone else’s cloud. Cloud platforms are someone else’s computers, and they aren’t in the sky. Surprisingly most operations decision makers I speak with assume that clouds are secure, because the providers say so. So if some country or criminal organization (sometimes that’s the same thing) wants to hack into industrial control systems of major industries to knock out their operations, why go directly at a company when a “cloud VPN security provider” offers a permanent back door to them, and virtual “buffet” of organizations’ sensitive industrial data and control systems.
The DragonFly attack was just that; a sophisticated and very well funded campaign targeting cloud VPN services. The SANS Institute InfoSec Reading Room has an excellent article entitled “The Impact of Dragonfly malware on Industrial Control Systems”, that I recommend reading. And while you are searching on SANS, please also read “Security in a Converging IT/OT World”, which gives some good insights as well.
IT may be the greatest risk to OT
I’ve already mentioned that IT and OT have cultural differences, and that IT’s approach to security may not be meeting the needs of the OT customer. I also mentioned that the best security for OT is physical isolation, so the thought of opening those systems to outside (particularly IT) networks is the top concern preventing the implementation of IIoT.
The most (in)famous attacks on Industrial Control Systems came from compromising IT systems. Stuxnet, the Shamoon attacks that took out Saudi Arabia’s National oil company, Aramco, operations (and multiple others), and the DragonFly attack, all came from compromising IT systems to gain access to OT systems. The secret to bridging the divide requires a bit of a paradigm shift – assume networks are already compromised then build completely secure tunnel connections inside those networks.
Developed over a decade ago, for a US Government program, Distrix creates highly secure and resilient operational networks to access sensor and system data safely around the world, under the assumption that networks are already compromised by adversaries. We’re now applying that philosophy to help networking and industrial control hardware providers meet the needs of their industrial customers and profit with confidence from IIoT.
You May Also Like
.jpeg?width=700&auto=webp&quality=80&disable=upscale)
.png?width=700&auto=webp&quality=80&disable=upscale)



.png?width=300&auto=webp&quality=80&disable=upscale)
