Recent research on IoT security risks from Ponemon Institute has startling conclusions about the C-suite’s focus on cybersecurity.
June 5, 2017

Today, the topic of industrial cybersecurity is something like the specter of ozone depletion decades ago. In both cases, there is a real risk that the problem — which is unseen by the average person but well understood by experts — poses a calamitous risk. In the case of the ozone discussions in the 1980s and ’90s, an act as seemingly innocuous as applying hair spray or flicking on a car’s AC contributed to the problem.
The corollary with the Internet of Things are the architects of industrial control systems who only wanted to help automate how machinery runs. “Their mindset was focused on building industrial automation tools that would operate for a lifetime,” says Peter Tran, senior director and GM of RSA. “But information technology came along and poked some serious holes in their ozone layer. As billions of new IoT sensors and devices come online, each of which is a new potential hole, that risk only gets bigger.”
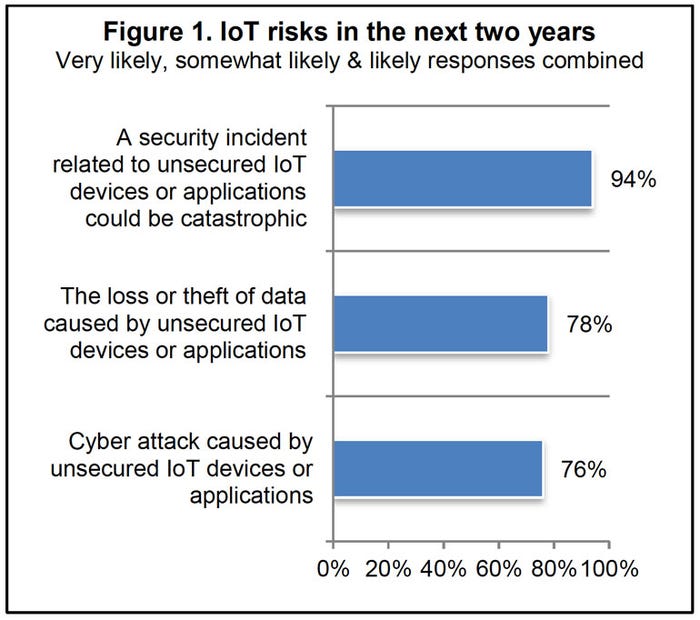
Security professionals across industries are all-too aware of IoT security risks. But recent research from Ponemon Institute indicates that the executives managing a variety of industries are not overly worried about it. Of the 553 security professionals surveyed, only 30% of survey participants reported that “managing third-party IoT risks” was a priority at their organization. Only one in four said their board of directors wanted assurances that such risks were being assessed and managed. Meanwhile, more than three-quarters of those professionals expected either an IoT-enabled data breach or DDoS attack to occur at their organization in the next two years, while 94% of them said such an incident would be catastrophic.
The most surprising finding from the research is that most industrial organizations do not keep an inventory of managed IoT devices and applications, says Gary Roboff, a senior advisor to The Santa Fe Group and Shared Assessments, which sponsored the research. In total, 16% of survey respondents reported that their organizations keep such an inventory. Two of the principle barriers in maintaining a catalog of IoT devices are the lack of centralized control over them (cited by 85% of survey participants) and the lack of resources to track those devices (cited by 56% of respondents). Forty-one percent of those participants said that an IoT inventory simply wasn’t a priority of their organizations. That’s a troubling finding. “If you don’t even have an inventory of which IoT devices are in your firm, how could you possibly secure them or mitigate risks associated with them?” Roboff asks.
Part of the problem is that cybersecurity is but one of the many risks business executives have to contend with. “At most organizations, financial matters, regulatory affairs, and other risks take precedence over cybersecurity,” says Charlie Miller, senior vice president of The Santa Fe Group and Shared Assessments. “The risk professionals on the ground see the [IoT security risks], but at many organizations, the top level isn’t really getting the message yet.”
“We have been looking at this issue for a long time,” says Larry Ponemon, Ph.D., chairman and founder of the institute bearing his surname. “Fifteen years ago, we saw a similar phenomenon.” Senior-level executives who are not in the IT organization haven’t typically thought of security as fundamentally strategic, he says. “But a company can’t really accomplish its business mission if it doesn’t have a fundamental level of security,” Ponemon adds. And yet, to be effective, security programs need support from upper management.
Addressing the problem will take both regulation and education, Ponemon concludes. Coincidentally, those two factors played an important role in combatting ozone depletion, forcing manufacturers to curb their use of ozone-depleting chlorofluorocarbons. The Montreal Protocol was perhaps the most successful environmental treaty in history and helped pave the way for the healing of the Antarctic ozone hole. “Clearly, some regulations are needed for IoT cybersecurity,” Ponemon says. Meanwhile, education needs to be an ongoing initiative. While an IoT-fueled data breach could serve as a wake-up call to an organization’s board of directors and CEO, it tends to elevate awareness for a limited period of time. Ponemon concludes: “If there’s a catastrophe and then, after a period of time, and you don’t get breached or have any discernable security problems for a while, you tend to go back to thinking that security isn’t the most important thing.”
About the Author(s)
You May Also Like


.png?width=700&auto=webp&quality=80&disable=upscale)
.png?width=300&auto=webp&quality=80&disable=upscale)


.png?width=300&auto=webp&quality=80&disable=upscale)